AWS GuardDuty Threat Detection Service
Amazon guard-duty could be a managed service that will threat detection showing the intelligence to safeguard the AWS accounts and workloads. It ceaselessly monitors for malicious or unwanted activities sort of a port scan, unauthorized penetration takes a look at etc. guard duty detects surprising behavior within the AWS atmosphere and generates notifications referred to as Findings that details the underlying security issue. AWS GuardDuty collects its inputs from 3 log streams. VPC Flow Logs, DNS logs, and CloudTrail events. Also, It will associate one AWS account with another account in order that you'll be able to read and manage their guard duty Findings on their behalf.
About the Experiment
I have added my laptop’s public informatics address to the AWS GuardDuty’s Threat list. Then I attempted to access AWS console associate degreed did an SSH to at least one of the EC2 instances of the AWS account, assumptive that guard duty will discover it. And it did it on behalf of me !!!
Configuration
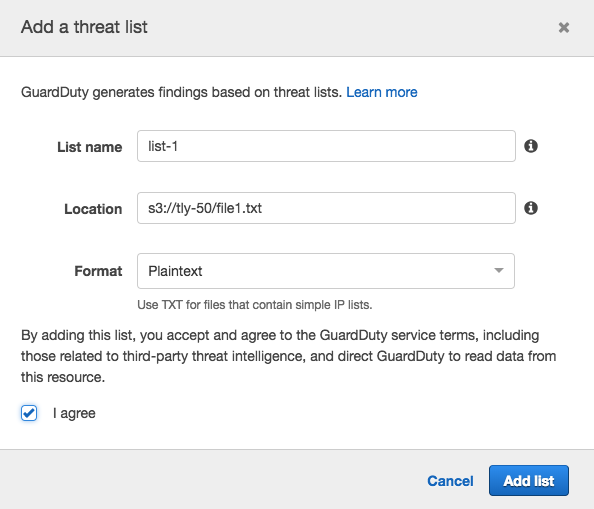
Create a file associate degreed add the “attacker” informatics address ( you'll be able to add multiple informatics addresses/CIDRs in every line) and transfer to an S3 Bucket. I actually have used file1.txt and uploaded to a bucket only-50, thereby uniform resource locator of the file s3://tly-50/file1.txt. ( I actually have hidden 1st 2 octets of the informatics address, however, you've got to put in writing in full)
2) Enable AWS guard duty by following screenshots below
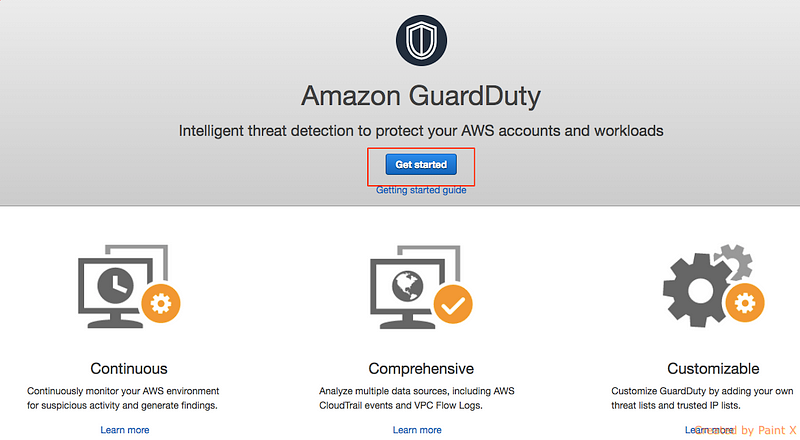
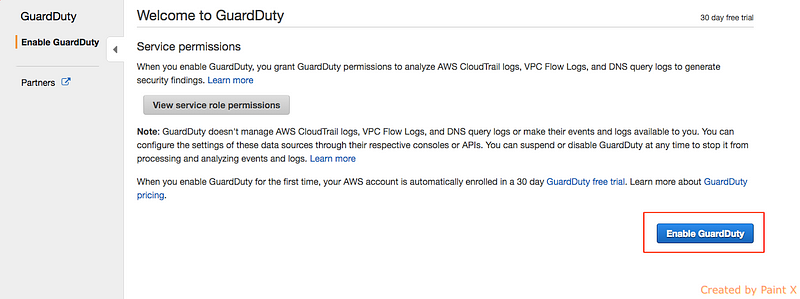
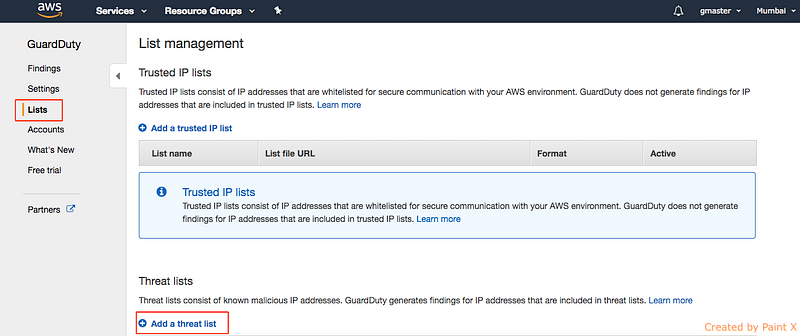
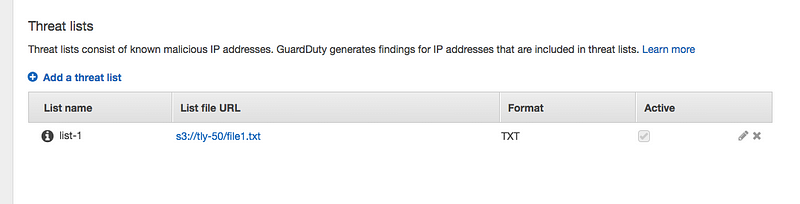
3) In the guard duty console click “Lists” and then “Add a threat list” like below
4) Create the threat list like below and add List Name, Location, and Format.
5) Make sure that List is activated. Now you are ready for testing
Testing the Setup
6) Login to AWS web Console from your the system whose IP address was listed within the threat list. Then you are trying to try to SSH to at least one of the EC2 instances within the AWS account. These are the 2 activities guard duty is predicted to notice.
7)After many minutes click the Findings. allow us to see the EC2 access Finding
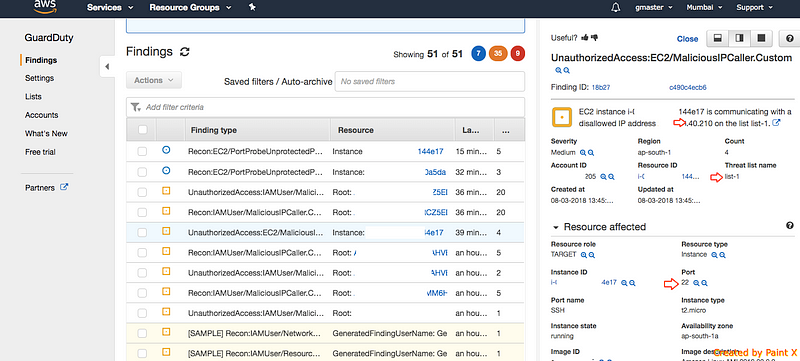
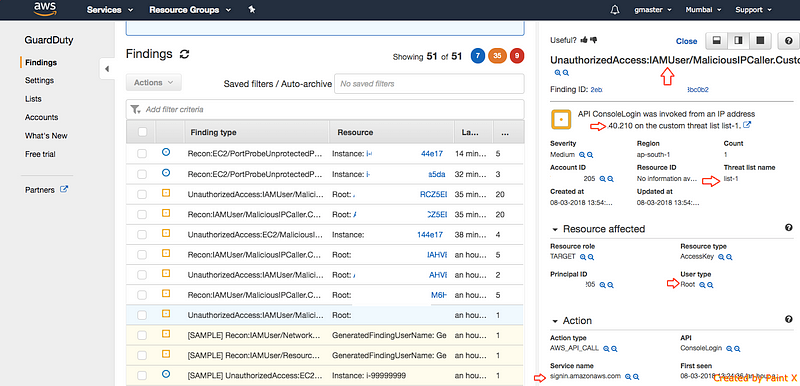
8) Now let us see how the AWS web console access is detected by GuardDuty.
Conclusion
AWS guard duty can detect and report malicious activities in the AWS account and workload. This is a managed service which identifies and reports undesired activities to the administrator. We have configured guard duty for threat detection and tested how it works.
Facebook
Twitter
Linkedin
Pinterest
Google+
Youtube
Altf9 Technology Solutions Pvt.Ltd
5/181, J4A Third Floor
Periyar Street, Medavakkam
Chennai, India
Pincode:600100.
INDIA: +91 8056005901
USA: +1 (845) 576-5295
Australia : +61291880753
info@altf9.in
Amazon guard-duty could be a managed service that will threat detection showing the intelligence to safeguard the AWS accounts and workloads. It ceaselessly monitors for malicious or unwanted activities sort of a port scan, unauthorized penetration takes a look at etc. guard duty detects surprising behavior within the AWS atmosphere and generates notifications referred to as Findings that details the underlying security issue. AWS GuardDuty collects its inputs from 3 log streams. VPC Flow Logs, DNS logs, and CloudTrail events. Also, It will associate one AWS account with another account in order that you'll be able to read and manage their guard duty Findings on their behalf.
About the Experiment
I have added my laptop’s public informatics address to the AWS GuardDuty’s Threat list. Then I attempted to access AWS console associate degreed did an SSH to at least one of the EC2 instances of the AWS account, assumptive that guard duty will discover it. And it did it on behalf of me !!!
Configuration
Create a file associate degreed add the “attacker” informatics address ( you'll be able to add multiple informatics addresses/CIDRs in every line) and transfer to an S3 Bucket. I actually have used file1.txt and uploaded to a bucket only-50, thereby uniform resource locator of the file s3://tly-50/file1.txt. ( I actually have hidden 1st 2 octets of the informatics address, however, you've got to put in writing in full)
2) Enable AWS guard duty by following screenshots below


3) In the guard duty console click “Lists” and then “Add a threat list” like below

4) Create the threat list like below and add List Name, Location, and Format.

5) Make sure that List is activated. Now you are ready for testing

Testing the Setup
6) Login to AWS web Console from your the system whose IP address was listed within the threat list. Then you are trying to try to SSH to at least one of the EC2 instances within the AWS account. These are the 2 activities guard duty is predicted to notice.
7)After many minutes click the Findings. allow us to see the EC2 access Finding

8) Now let us see how the AWS web console access is detected by GuardDuty.

Conclusion
AWS guard duty can detect and report malicious activities in the AWS account and workload. This is a managed service which identifies and reports undesired activities to the administrator. We have configured guard duty for threat detection and tested how it works.
Google+
Youtube
Altf9 Technology Solutions Pvt.Ltd
5/181, J4A Third Floor
Periyar Street, Medavakkam
Chennai, India
Pincode:600100.
INDIA: +91 8056005901
USA: +1 (845) 576-5295
Australia : +61291880753
info@altf9.in



Comments
Post a Comment